How to Make Remote Keylogger Undetectable from Antivirus with FUD Crypter
|
|
What is a Crypter?
Crypter is a special type of software used to hide viruses, malware, keyloggers or tools from Antiviruses as to make it fully undetectable. Thus, a Crypter is a program that allow users to crypt the source code of their program to Bypass antivirus detection mainly. Therefore our crypted file becomes UD (undetectable) or FUD (fully undetectable).
Features of this Crypter- Star Crypter Public V1.2:
1. Unlimited File Crypter
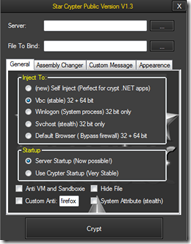
Right Click on the box in the main to browse for a file, after clicking "Add File". Or just drag and drop your files. You can crypt and FUD native and managed (.NET) files. A file can be deleted by right clicking on one file and clicking on "Delete". You can delete multiple files at once by selecting them. You can crypt any file, even .pdf, .doc, .gif etc.
2. Unlimited File Binder
Binding is the same as browsing for multiple files. Just browse multiple times and add those files to the list or simply drag and drop them. You can even bind executables with .Pdf's, managed files, pictures and anything you want! If you want to run an executable file only once when startup is checked. Then rename the file from .exe to .com before you bind it.
3. Change Assembly Information
You can Change the Output information to make the file look more legit. You can save your custom information, use one of the 10 pre-typed ones, import information out of a file, or just generate random strings. In some cases, legit assembly information can lower the detection rates.
4. Change Icon
Changing Icon make the outputs look more professional and in some cases it gives more Undetected Outputs. You can import ".ico" files (recommended) or clone the icon of a file.
5. Pump File
This adds bytes to the output to increase the size of it. You can add in kB and MB.
6. Spoof Extension
Spoofing extension will only work on Windows Vista and Win7. It is recommended to use short output names. The computer should also show all file extensions in order to work. With the right combination of assembly information and Icon it can be effective to trick someone and make him believe the .exe is actually an .mp3 or any other extension that you can type in the box.
You can also just save the file as .bat .com .scr .pif using the "Build"-button. This is not extension spoofing and this will work on all computers.
7. Fake Message
The message that you type here only starts once. Even if you have startup enabled. It supports multi-line and you can choose the buttons and style you want.
8. Hide File
On execution, the file goes hidden and removes itself. But it stays in the same path and if a user has "show hidden files", the file will just be there.
How to Use it?
1. First of all download and install this software from here.
2. Now Open the FUD Crypter select server file as your Keylogger file or RAT file, then go to Appearance tab- check custom icon and select your icon respectively.
3. Finally click " Crypt " and you will get a Crypted file which is totally undetectable by antiviruses.
4. All Done! Now send this crypted file to your victims and enjoy remote keylogging with crypter powered.
AV Scan Results :-After crypting my remote keylogger made file with star crypter public V1.2, I found zero viruses results as per Norton Antivirus.
Any Help Required?
If you have any doubts regarding the article, Please feel free to post an comment just below.
Join me on Google+
|
|
Respected Readers :-
|

E njoyed this post very much – So why not you Subscribe to our regular Email Updates ! and stay connected with us forever .


















thre is virus in the crypter
ReplyDeleteYa dont worry about that as every crypter/binder comes with some viruses.
Deleteok i hope you are still around cause i have QUESTIONS! i am VERY new to this world (like maybe 28hrs :) ) but in this time i have created an ardamax keylogger attached to a pic (jpg) crypted/binded with CHROME researched how to use CMD to make the keylog hidden then copy to the pic in one attachment and then sent via tagged email so that i would know when it was opened. It was about 10 min later (oh yeah FTP on drivehq) SOOOO what did i do wrong???? I have uninstalled EVERYTHING so that i can start from scratch.... so i downloaded this crypt....what is my server file? (simple terms i am not tech savy but quick learner, quite creative, imaginative and a lil sneaky~ I AM LIKING THIS :)) and what is a good file? am i to reinstall ardamax (is that my keylog server file???) what do you recommend using as the install file? then what do you recommend as attaching and getting them to open????
ReplyDeleteok thats a start! I appreciate any help/ suggestions.....
TIME IS OF THE ESSENCE :)
I am looking for way to hack/keylogg IPAD, is this even possible, can anyone help? please respond frkylilroleplayr@yahoo.com
ReplyDeleteAegis Crypter 8.1 PAID STUB|FUD crypter|free fud crypter |
ReplyDeletehttp://bicombusiness.blogspot.com/2016/01/aegis-crypter-81-paid-stub.html
it won't introduce because of some remaining documents from the past antivirus program at that point download the past introduced antivirus programs removal utility from the merchant's site and run it. click the up coming website page
ReplyDeleteOn the off chance that you resemble numerous you redesigned or plan to move up to Windows Vista.Windows USA Arkansas Windows Tips
ReplyDeleteThe sheer size and effectiveness of the web too its billion or more clients makes new PC infections more perilous and harmful than any other time in recent memory. Techpally.com PC virus clean
ReplyDeleteac
After you have downloaded and introduced Revo Uninstaller, use it to uninstall your current antivirus program. Check pages 6-9 of the assistance manage by tapping on the assistance tab on the Revo Uninstaller menu bar to take you through the uninstall methodology. norton discount
ReplyDelete